Introduction
Traditionally, enterprises have provided virtual private networks (VPNs) for remote employee access, but this model is now facing widespread challenges. According to Tailscale’s latest “The State of Zero Trust 2025” whitepaper, the data is telling:
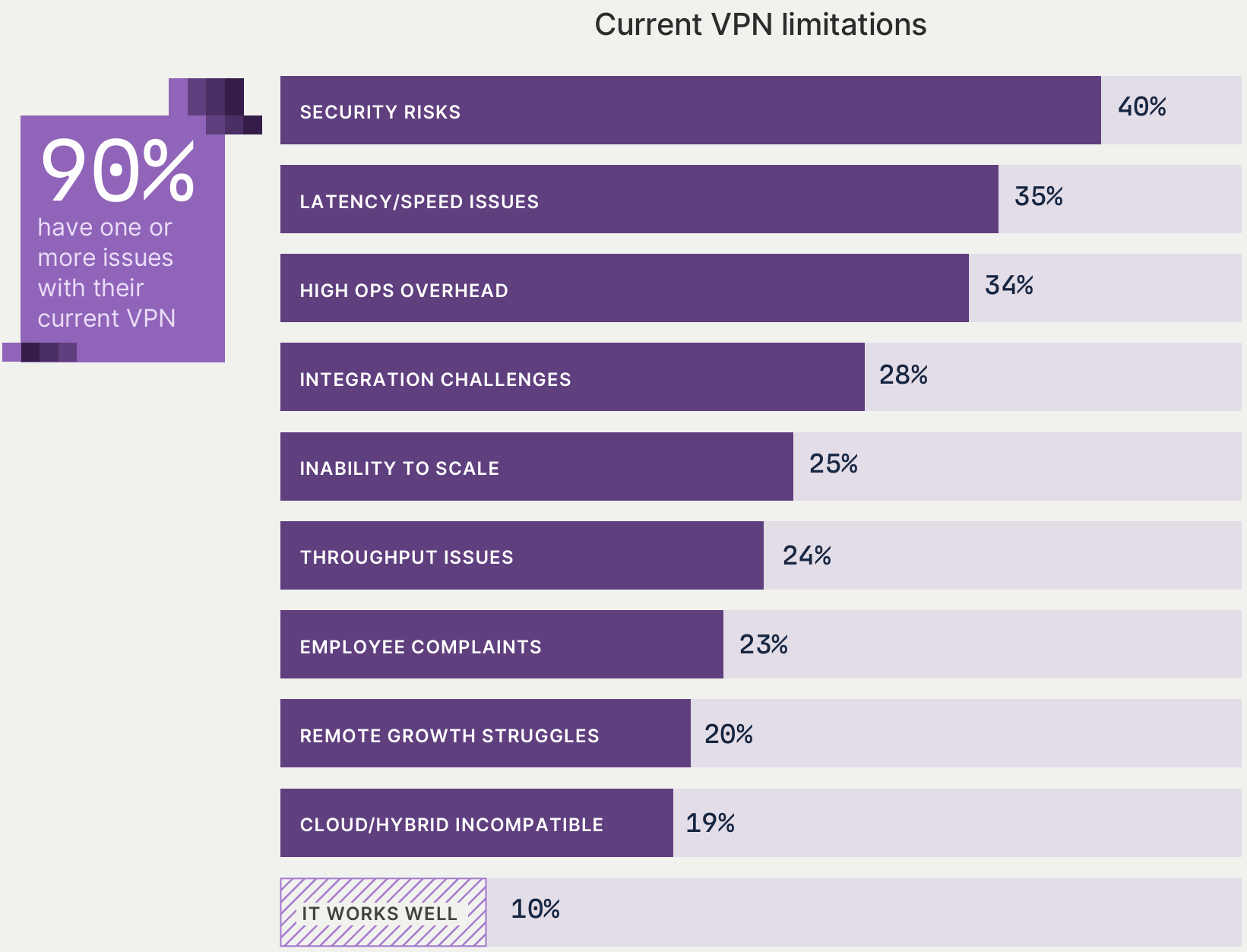
- Up to 90% of organizations have encountered at least one problem with their existing VPN.
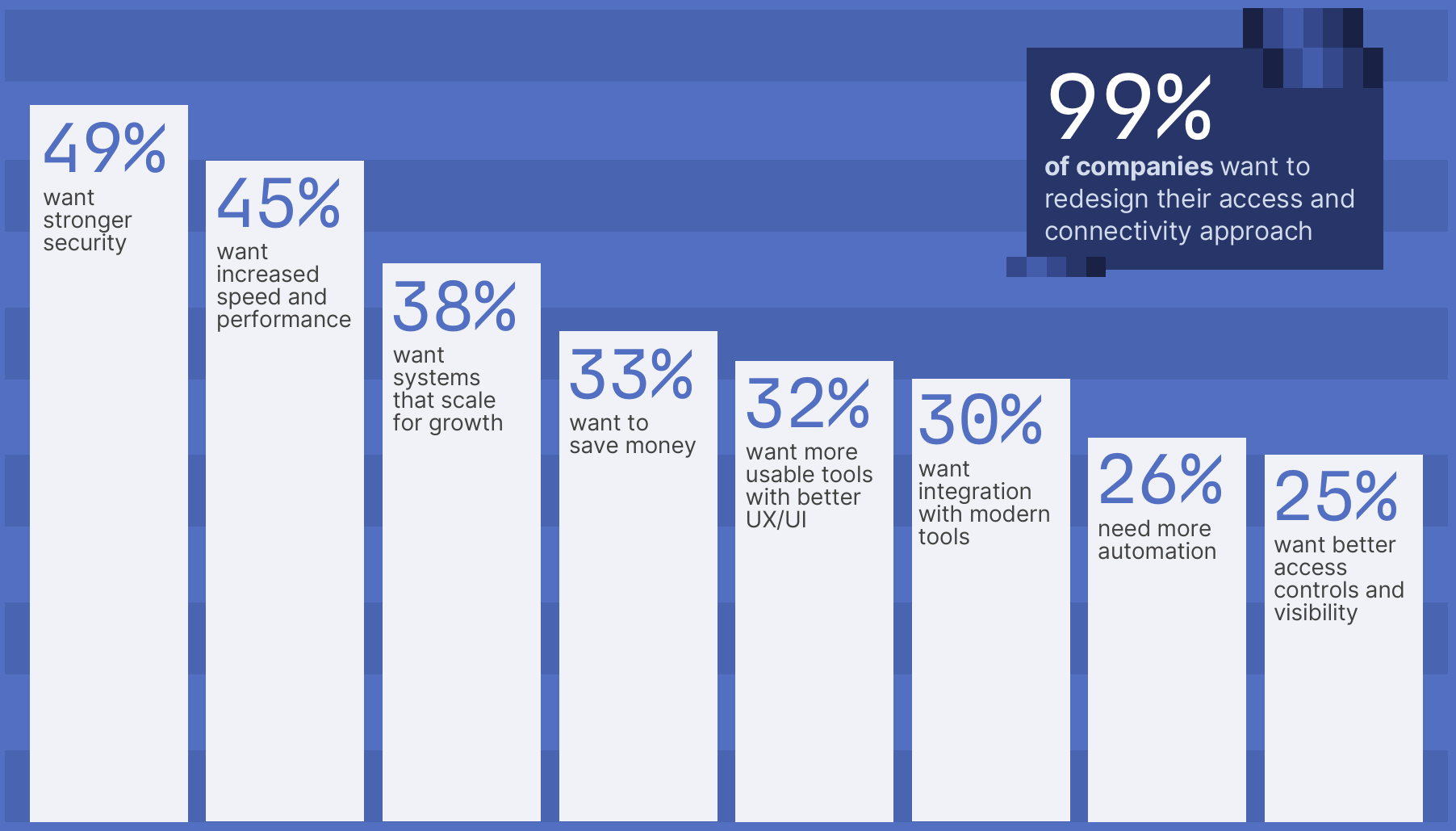
- An even more striking 99% of companies want to redesign their access and connectivity methods.
These statistics clearly indicate that the traditional “castle-and-moat” network security model has reached a dead end. The legacy architecture, which divides the network into a “trusted internal” and an “untrusted external,” can no longer effectively thwart threats in today’s environment of hybrid work, cloud services, and mobile devices.
This article aims to explore the limitations of traditional VPNs and use a common, practical case study—accessing files on an internal network-attached storage (NAS) device from the public internet—to illustrate how a Zero Trust architecture solves these pain points.
The Inherent Challenges of the Traditional VPN Model
The original purpose of a traditional VPN was to bring remote users “back” into the corporate network, making it seem as if they were physically in the office. However, this design introduces three inherent flaws:
- Overly Permissive Access: Once connected to the VPN, a user typically gains broad access to the entire internal network, far exceeding what is necessary for their job.
- Significant Security Risks: In the whitepaper, 40% of respondents listed “security risks” as the top problem with VPNs. If VPN credentials are compromised, an attacker effectively holds a master key to the entire organization. They can roam freely within the internal network, performing lateral movement to find their next target.
- Performance Bottlenecks and Poor User Experience: All remote traffic must be backhauled through a central gateway before being routed to its destination. This creates high-latency, bandwidth-constrained pathways that severely impact overall productivity.
Real-World Case: Accessing a Corporate NAS Consider an employee accessing a project file on an internal NAS from home:
- The employee launches the VPN client, enters their credentials, and successfully connects, making their computer a part of the internal network.
- If an attacker steals these credentials, they can not only access the NAS directly but also scan for and attack other internal servers and databases.
- This is a classic example of a lateral movement risk.
A Zero Trust architecture is designed to prevent this kind of implicit, location-based trust by granting users only the minimum access they require.
Core Principles and Enabling Technologies of Zero Trust
Zero Trust is a modern security model built on the core philosophy of “Never Trust, Always Verify.” It discards the traditional assumption of a trusted network perimeter and is founded on three principles:
- Verify Explicitly: Every access request, regardless of user or device location, must be strictly authenticated and authorized.
- Use Least-Privileged Access: Grant users only the minimum permissions necessary to perform their work, drastically reducing the potential attack surface.
- Assume Breach: Operate under the assumption that any part of the network (internal or external) could be compromised, requiring continuous monitoring and verification.
Technically, Zero Trust Network Access (ZTNA) is the core technology that enables these principles. Its operational model is fundamentally different from that of a traditional VPN:
- Traditional VPN Access Model: Connects an authenticated user to the entire trusted corporate network. This is like giving a user a master key that opens every door in the building, exposing them to resources they don’t need.
- ZTNA Access Model: Creates a unique, protected access tunnel for each application or resource. It only establishes a connection between a user and a specific resource after successful verification. This is like giving a user a key that opens only one specific room, not the entire building.
According to the whitepaper, 68% of respondents retained access to some company systems after leaving their jobs. Of these, only 32% had their access removed on their last day. 22% were removed within days, 27% within weeks, 13% after months, and 2% had to wait years for their access to be revoked.
Practical Implementation of a Zero Trust Architecture
Using internal NAS access as an example, an IT administrator following Zero Trust principles can choose from various technical paths. Tailscale and Cloudflare Zero Trust are two of the most well-known approaches.
Tailscale
Core Mechanism: Utilizes a peer-to-peer encrypted network (a “Tailnet”) based on WireGuard, ensuring end-to-end encryption for all device-to-device communication. Relay servers cannot inspect traffic content.
Client-Side Setup: Admins install the Tailscale application on each device. Users log in via a corporate identity provider (e.g., Apple, Google, Github, Microsoft, Okta) to add their device to the Tailnet.
Traffic Path: Ideally, traffic flows directly between devices via a peer-to-peer connection for low latency and high performance. If NAT traversal fails, traffic is automatically relayed through Tailscale’s DERP (Designated Encrypted Relays for Packets) servers while still maintaining end-to-end encryption.
Access Method: Tailscale automatically assigns a
100.x.y.zvirtual IP address to each device and can be paired with its MagicDNS feature to enable access via device names, simplifying host resolution and connection configuration.Authorization: Admins can use the Tailnet’s access control list (ACL) mechanism to define least-privileged access rules in a policy file. These rules are based on user identity, groups, or device tags and follow a deny-by-default principle.
Cloudflare Zero Trust
Core Mechanism: Shifts the traditional network perimeter to Cloudflare’s global Anycast network. It enforces identity and security policies in the cloud before connecting users to internal resources.
Client-Side Setup: Users can either install the Cloudflare WARP client (which directs device traffic to the Cloudflare cloud for Gateway and Access policy enforcement) or use the clientless browser access mode to access web applications without installing any software.
Traffic Path: All requests are first routed to the nearest Cloudflare Point of Presence (PoP). Cloudflare performs identity authentication, device posture checks, and security scanning in the cloud. Once verified, traffic is securely routed to the target resource via a Connector deployed in the private network.
Access Method: Users access resources through private or public FQDNs (fully qualified domain names) proxied by Cloudflare. DNS resolution and connection control are managed by Cloudflare, and access is only granted after passing identity and security policies.
Authorization: In the Cloudflare dashboard, admins can define multi-conditional authorization policies through Cloudflare Access. These policies can be based on user identity, geographic location, device posture (e.g., WARP client installed, disk encryption enabled, antivirus version), and network attributes to enforce the principle of least privilege.
Comparison
| Feature | Traditional VPN | Tailscale | Cloudflare Zero Trust |
|---|---|---|---|
| User-Side Setup | VPN Client → Connect | Install App → SSO Login → Auto-reconnect | WARP Client or Browser-based Access |
| Traffic Path | User → VPN Gateway → Internal Network | Peer-to-peer (falls back to DERP relays) | User → Cloudflare Anycast → Connector |
| Access Method | Internal IP / Subnet | 100.x Virtual IP or MagicDNS Name | Private FQDN (proxied by Cloudflare) |
| Authorization | Allows all internal traffic | IdP Identity + ACLs (Least Privilege) | Multi-conditional policies (Identity/Device/Location) |
| Deployment Complexity | Medium | Low (Plug-and-play, no network changes required) | Medium to High (Requires Connector deployment, DNS changes) |
| Auditability | Requires separate log server | Supports SSH proxying and session recording | Real-time export with Cloudflare Logpush |
| Scalability | Limited by gateway performance | No central hub, highly scalable | Auto-scales with Anycast network nodes |
| Cost Control | Appliance and bandwidth costs | Per user/device, no extra hardware | Based on traffic and number of policies |
| Free Plan | Requires self-hosted server (OpenVPN, SoftEther) | Up to 3 users, 100 devices | Up to 50 users (paid upgrade required beyond that), no device limit |
Conclusion
The limitations of traditional VPNs are accelerating the adoption of Zero Trust architecture. This is no longer a future vision but an ongoing security paradigm shift. This article has explored the risks of traditional access models and demonstrated how modern solutions like Tailscale and Cloudflare Zero Trust can turn the “Never Trust, Always Verify” philosophy into a reality with readily available tools. For both individual users with generous free plans and enterprises seeking rapid, pay-as-you-go deployments, Zero Trust is no longer an out-of-reach blueprint but a best practice that can be adopted today.
The core of this transformation is shifting the basis of trust from ambiguous network perimeters to explicit digital identity. Whether through a peer-to-peer Mesh VPN or a cloud-proxied ZTNA, the common goal is to achieve least-privileged access, ensuring every connection is rigorously verified and thereby eliminating pathways for lateral movement.
When identity becomes the new cornerstone of security and artificial intelligence empowers defensive systems to adapt in real-time, security will no longer be an obstacle to productivity. Ultimately, the goal of Zero Trust is to create a digital environment that is secure by default and seamlessly integrated. For all enterprises, now is the time to abandon the traditional castle-and-moat mentality and embrace Zero Trust. Only then can they enhance security while empowering their teams with unprecedented agility and resilience, achieving a true win-win for security and efficiency.
For individual users who want to get started but feel intimidated by technical terms like VPN, NAT traversal, reverse proxies, or NAT hole punching, the first step is actually very simple. By following the installation guide in my previous article, “Using Tailscale to Easily Create Secure and Private Tunnels,” you just need to log in to the app on two devices with the same account to establish a secure, peer-to-peer connection. It’s that easy. Congratulations—you’ve just created your own Zero Trust network.
This simplicity embodies the core of Zero Trust: everything is authenticated based on identity. As soon as you log out, the connection is terminated. Extending this model to the enterprise, employees authenticate via an identity provider like Okta, Microsoft Entra ID, or Google Workspace. An IT administrator simply needs to disable an employee’s account in the IdP, and their access to all applications is revoked instantly and automatically, without having to manually de-provision permissions in each system. This dramatically improves both security and administrative efficiency and allows for more complex policy enforcement to build a comprehensive and dynamic Zero Trust architecture.
